Remote Server Management
Software Based vs. Embedded Service vs. KVM-Over-IP

Important facts to consider when choosing your tools
Table of Contents -
Remote Server Management
- Remote Server Management Overview
- Four Criteria for Selecting your Remote Server Management tools
- Software-based Remote Server Management Systems
- Embedded Service Processors
- KVM-over-IP Switches
- Remote Server Management Tool Comparison Based on Four Criteria
- Why KVM-over-IP Switches Should Be Your Remote Server Management Tool

Remote Server Management Overview
As an IT administrator, Lab or Network Manager, you need to access and control multiple computer systems, perhaps widely dispersed, for routine maintenance as well as for real-time troubleshooting and repair. The tools must enable you to work quickly and securely to access any system regardless of type, brand, or location.
Remote server management tools fall into three general categories:
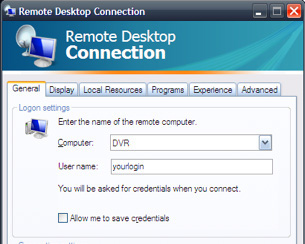
Software-based remote access systems
(e.g. RDP, VNC)
Computer embedded service processors
(e.g. iLO, DRAC and RSA)

Out-of-band KVM-over-IP switches
(e.g. Dominion KX3 from Raritan)
While these categories merely describe how the tool itself is physically deployed, it is critical to understand the inherent advantages and limitations of the tools in each category in getting the job done.
How to make the best choice?
Four Criteria for Selecting your Remote Server Management tool
Fortunately, these tools have been deployed for several years, so there is an abundance of real life experience and data to draw upon. There are four basic criteria to always consider when selecting a Remote Access and Control tool.
Is it..?
- Reliable check Will my remote access and control work when I need it most?
- Secure check Is my remote access and control tool safe from hackers and cyber attack?
- Manageable check Is my remote access and control tool easy to manage and maintain?
- Power check Can I access and control all my devices wherever they are and perform all my day-to-day tasks?
How does each of the three categories stack up?



Software-Based Remote Server Management Systems
Overview
- Software applications installed on each target computer
- Typical systems in this category include RDP, VNC, pcAnywhere
- Can be free to acquire – e.g. RDP, VNC
- No hardware to install
But consider ...
- Software must be installed and maintained on every computer to be accessed
- Requires the Target Computer OS and production network to be running properly
- Does not provide BIOS-level access, which may be required for reboot or other emergency action
- Competes with production applications for system resources
- Well-documented security risks.
- Poorly configured remote access is responsible for 62% of security breaches
- 83 million open VNC ports and 230 million open RDP ports
Bottom Line
- Although commonly used, it has limited capabilities and presents security issues
Embedded Service Processors
Overview
- Hardware-based remote access built into the computer
- Examples: HP iLO, Dell DRAC, IBM RSA
- Provides BIOS level access, virtual media and power control
- Can be an out-of-band solution using a separate LAN port
But consider ...
- Must pay a license fee for advanced features standard on KVM-over-IP switches
- Requires an additional LAN port for out-of-band access
- Difficult to manage 100's of service processors
- Nightmare to manage with multi-vendor systems and service processors
- Recent research has highlighted shocking vulnerabilities
- Possible to login with no authentication, cleartext passwords, etc.
- Department of Homeland Security issued CERT Alert (TA13-207A)
Bottom Line
- Good performance, but hidden costs, difficult to manage and presents security issues
Remote Server Management Tools
| Customer Need | Software Access | Service Processor | |
|---|---|---|---|
security Secure | star_borderstar_border | star_border | star_borderstar_borderstar_borderstar_border |
memory Performance | star_borderstar_border | star_borderstar_borderstar_borderstar_border | star_borderstar_borderstar_borderstar_border |
star Reliable | star_border | star_borderstar_borderstar_borderstar_border | star_borderstar_borderstar_borderstar_border |
laptop Manageable | star_borderstar_border | star_borderstar_border | star_borderstar_borderstar_borderstar_border |

Why KVM-over-IP Switches Should Be Your Remote Server Management Tool
memory High Performance - just like being there
- BIOS-level Remote Access
- Virtual Media, including Remote Booting
- Option for remote power control
security Secure - the most secure remote access method
- Independent security barrier to target computers
- Military-grade security and encryption
star Reliable - reliable when you need it most
- Not dependent on target computer OS or network
- True out-of-band access - connects via KVM ports
- Optional modem access
laptop Manageable - easy to manage and maintain
- Up to 64 times less configuration/maintenance
- Centralized access, management & logging
We offer a large variety of KVM-over-IP Solutions for any application!
Vendor Independent | 25-Years of Experience | We're Here to Help!

Need Help Choosing an IP KVM? We're Here to Help!






